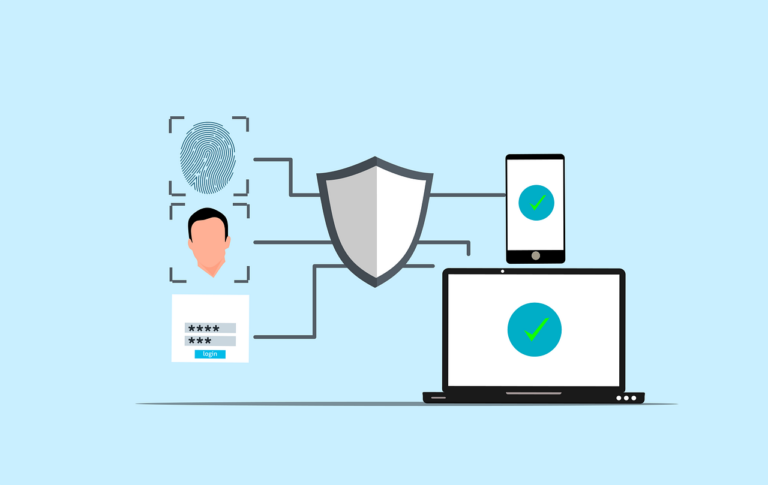
Have you ever wondered how vulnerable your business is to cyberattacks? According to recent reports, nearly 43% of cyberattacks target small businesses, often exploiting weak security measures. One of the most overlooked yet highly effective ways to protect your company is through Multi-Factor Authentication (MFA). This extra layer of security makes it significantly harder for […]
7 Unexpected Ways Hackers Can Access Your Accounts
The digital age has made our lives easier than ever, but it has also made it easier for hackers to take advantage of our online weaknesses. Hackers are getting smarter and using more creative ways to get into people’s personal and business accounts. It’s easy to think of weak passwords and phishing emails as the […]
How Do Websites Use My Data? (Best Practices for Data Sharing)
Websites store and use user data in many ways, usually to personalize content, show ads, and make the user experience better. This can include everything from basic data like the type of browser and IP address to more private data like names and credit card numbers. It’s important for people to know how this information […]
What is Password Spraying?
Password spraying is a complex type of cyberattack that uses weak passwords to get into multiple user accounts without permission. Using the same password or a list of passwords that are often used on multiple accounts is what this method is all about. The goal is to get around common security measures like account lockouts. […]
7 New and Tricky Types of Malware to Watch Out For
Malware is a huge threat in the digital world. It can cause a lot of damage and cost people a lot of money. As technology advances, so do the tactics used by cybercriminals. In this article, we will explore some of the newest and trickiest types of malware. 7 Malware Threats to Watch Out For […]
- « Previous Page
- 1
- 2
- 3
- 4
- …
- 9
- Next Page »